Think Like a Hacker! Protect Your PBX – Part 1: Recon
The modern Internet landscape can be a landmine for the uninitiated. In order to keep an internet-facing PBX secure and on-line, you need to be aware of the security implications, and be able to manage them. This series of security-related articles will assist you in increasing the security and protection level of your PBX. The same principles and guidelines can be applied to any other system or network that you manage.
In part 1, we address the activity of reconnaissance (recon) and info gathering as the first phase in hacking methodology.
Here be Dragons: The Current Security Landscape

Let’s start with some facts to provide a better understanding of the current environment that your system operates in:
- Connecting a system with a public IP will immediately open it up to a barrage of automated bot scans. These bots seek to identify the running software and any open ports on your system, for a more targeted attack against discovered vulnerabilities.
- The software or hardware you use, can and will be used against you (pun intended). System software and hardware vulnerabilities, disclosed or not, define your main exposure to attacks against your system(s). Such vulnerabilities can include but are not limited to:
- Compromises made during the design phase, e.g. hidden and/or unsecured remote administration ports and APIs (Application Programming Interfaces).
- Undisclosed software and/or hardware vulnerabilities, e.g. backdoored or eavesdropping utilities.
- Lax security measures susceptible to snooping, e.g. unencrypted data transmission over FTP, HTTP, email.
- Most successful hacks are not disclosed and/or acknowledged. Gone are the days of publicly defaced servers for fun and games. These have been replaced with malicious, covert and long-enduring system take-overs with more serious intent and purpose. A typical case is an attack where data is kept hostage or threatened to be publicly exposed, unless ransom is paid to the perpetrators.
- Compromised systems are worth a lot to malicious actors, as they can be used for a variety of purposes. The Dark Web is host to a number of obscure marketplaces where access to compromised servers and confidential info is bargained, bought and sold for virtual currency.
- Phishing and other social engineering tactics make up a lucrative day-to-day activity for cyber fraudsters. Their main objective is siphoning user/admin credentials from users via emails, calls or even in-person visits.
- The “fifth column” factor presents the very real and challenging risk of trusted insiders, using their privileged access for purposeful tampering and/or malicious intent. These individuals can wreak havoc in various ways, most commonly exfiltrating confidential data while going unnoticed.
Phase 1: Recon(naissance) & Information Gathering
The main objective of recon activity is to analyze any info on your network and/or devices to gain valuable insights. This learning process ultimately aims at locating the “path of least resistance” to gain entry and compromise a target. Essentially a recon operation is scanning a target network or system with the aim of attacking in a much more precise and stealthy manner. Just like the hunter studies the behavior of its prey before the attack.
Recon Methods
For a VoIP target, in particular, the attacker may be interested in gaining info on network hosts/servers, including types and versions for PBXs, VoIP media gateways, and SIP clients. Reconnaissance is a critical part of the hacking methodology and is used as the basis for all subsequent actions. To hack a system you have to first identify its existence and its characteristics. Recon can be categorized into these activities:
Passive
In passive mode an attacker gathers information without interacting directly with the target. Using OSINT (Open-source intelligence) they can discover information about both internal and external networks through publicly available sources. This extremely powerful method can yield results from various sources, such as public IP and DNS history, WHOIS databases, cloud storage buckets and social media accounts. Be aware that any piece of info that you make public is of value to someone, somewhere.
Active
Scanning
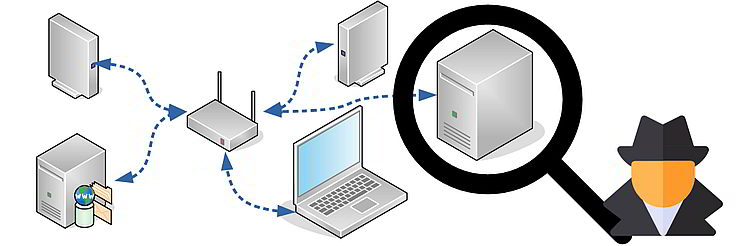
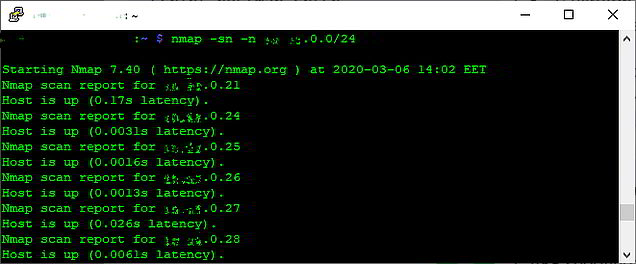
In active mode, an attacker interacts directly with the target in order to identify points of interest. This includes scanning any services/endpoints found in an attempt to identify live systems, open ports, and services that may be running, including their version. For instance, you may identify the software a server/service is running, by simply checking its specific listening ports and/or by checking for a web interface advertising its make/version. Other typical actions include mapping network and devices using tools like “nmap”, or spoofing ARP (Address Resolution Protocol) messages in LAN devices to perform an MITM (Man In The Middle) attack.
Social Engineering

Another method of gaining valuable information about a target is Social Engineering. This requires a direct email, telephone, or personal contact with a targeted person-of-interest. For instance, calling an employee as a tech support technician and requesting some sensitive or confidential info under the guise of resolving an issue. Social Engineering is directly related to phishing methods.
Sniffing
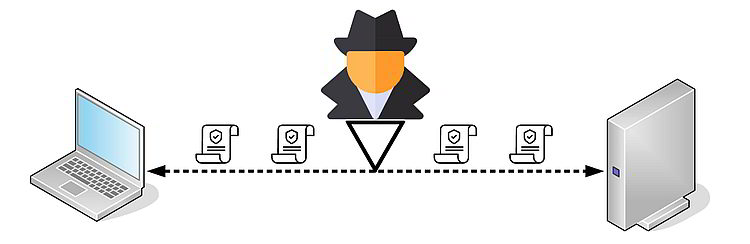
This method aims to capture packets over the local network. An attacker uses various methods to receive packets destined for other devices and examines them to identify sensitive info, such as usernames, passwords, keys, and files.
With the information gathered using the above methods, an attacker can now proceed with the enumeration process. The objective in enumeration is to gather/extract additional information from the various identified services, including users, emails, directories, hostnames, network shares, applications, and more. A common occurrence in VoIP is default credentials being used in appliances such as gateways and/or IP phones.